In my last post, I wrote about how a party might authenticate a Facebook direct message or other text-based electronic communication. That post focused on how the proponent of the evidence might establish who wrote the message, i.e., authorship. But what if a party wants to introduce a photograph that was posted on a social media platform? The concept of authorship doesn’t really apply, and in the age of Photoshop and AI-generated images, courts may have serious concerns about the accuracy of online images.
social media
How Can a Party Show Authorship of a Social Media Post or Other Electronic Communication?
Suppose that a defendant is charged with possessing fentanyl with the intent to sell it. The state’s evidence includes a Facebook direct message, purportedly from the defendant to an informant, saying “just got some China Girl, you want any?” An officer took a photograph of the direct message as it appeared on the informant’s smartphone, and everyone is satisfied that the photograph fairly and accurately depicts the message. But the defendant objects to the introduction of the message on the grounds that there’s no way to be sure that he wrote it. How might the state respond?
Online Impersonation
If you haven’t, Catfish is a TV show that uncovers stories of online romantic relationships in which one person is involved with (and has usually sent money to) another person they have never seen. Some of the “couples” will have communicated online for several months without having ever seen one another, and the investigation usually reveals that the person on the other end was not who they claimed to be.
The show gave rise to the popular term “catfish,” which Merriam-Webster defines as the act of deceiving someone by creating a false personal profile online. Though it may be the most common, catfishing is merely one form of online impersonation. While many people may find it entertaining, catfishing and other methods of online impersonation can come with serious consequences.
New Guidance on Authenticating Social Media
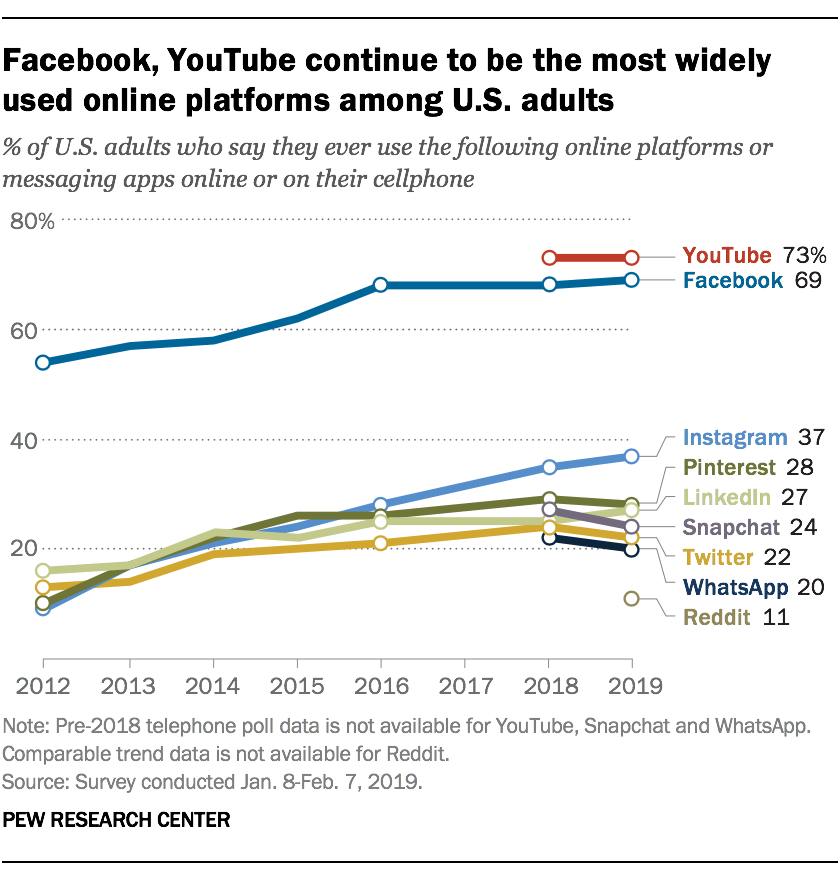 Nearly half of the 7.7 billion people in the world are on social media, and each of those users has an average of 8 different accounts. The rate is even higher in the U.S., with around 70% of the population active on social media for an average of 2 hours every day. You can find more jaw-dropping statistics here.
Nearly half of the 7.7 billion people in the world are on social media, and each of those users has an average of 8 different accounts. The rate is even higher in the U.S., with around 70% of the population active on social media for an average of 2 hours every day. You can find more jaw-dropping statistics here.
Given these trends, it’s no surprise that social media evidence is showing up more frequently in criminal cases. A quick search for criminal cases mentioning the most common social media platforms brought up well over 100 North Carolina cases decided in the last decade, but only a few of those cases have directly analyzed the authentication requirements for this type of evidence. The Court of Appeals recent decision in State v. Clemons, __ N.C. App. __ (Dec. 1, 2020) provides some additional guidance in this important area.
State v. Thompson Tells a Tale of Two Facebook Screenshots
 After Roshawn Thompson picked up his cousin Kendall Rascoe from the Greenville mall in November 2014, Thompson and a friend, Andre Grey, robbed Rascoe at gunpoint. At Thompson’s armed robbery trial, his defense attorney sought to cross examine Rascoe about Facebook messages he sent to Thompson earlier in the day asking whether Thompson could get some marijuana for him while he was in Greenville. Rascoe denied sending the message and testified that he just happened to run into Thompson at the mall. The State objected to the admission of the screenshot of the messages.
After Roshawn Thompson picked up his cousin Kendall Rascoe from the Greenville mall in November 2014, Thompson and a friend, Andre Grey, robbed Rascoe at gunpoint. At Thompson’s armed robbery trial, his defense attorney sought to cross examine Rascoe about Facebook messages he sent to Thompson earlier in the day asking whether Thompson could get some marijuana for him while he was in Greenville. Rascoe denied sending the message and testified that he just happened to run into Thompson at the mall. The State objected to the admission of the screenshot of the messages.
Later in the trial, the State sought to introduce a screenshot of a picture of Thompson and Grey copied from Thompson’s Facebook page. Rascoe showed the investigating detective the picture for purposes of identifying Thompson and Grey. Thompson objected to the admission of the screenshot, in which both of his middle fingers were extended.
How did the trial court rule? Did it make the right call?
May an Officer Assume a False Identity Online in Order to “Friend” a Suspect?
Officers are allowed to misrepresent their identities in the course of their investigations: they may pose as drug buyers, or prostitutes, or members of an organized crime syndicate. Is the same thing true online? In other words, may an officer claim to be someone else in order to “friend” a suspect on social media and thereby gain access to whatever information the suspect has posted? The answer isn’t clear yet, but I would guess that courts ultimately will say yes.
Court of Appeals Upholds Admissibility of Social Media Evidence Based on Circumstantial Evidence of Authenticity
The court of appeals recently decided State v. Ford, a case about the authentication of social media evidence. This is the first North Carolina appellate case to give careful consideration to the issue, and the opinion sets a relatively low bar for authentication. Because this type of evidence is increasingly prevalent, the case is an important one.
Legal Ethics and Social Media
The number of lawyers using Facebook, Twitter, LinkedIn and other social media networks grows daily. So too does the number of lawyers doing foolish and unethical things on those networks.
In this post I highlight some of the more egregious social media missteps made by lawyers in recent years, in the hope that other lawyers won’t repeat them. Then I describe how the Rules of Professional Conduct apply to social media both generally and in specific contexts such as investigations, litigation, and client testimonials.
The State Bar Addresses Lawyers, Judges, and Social Media
The North Carolina State Bar recently adopted 2014 FEO 8, an ethics opinion concerning lawyers’ and judges’ use of social media. The opinion answers some questions, but raises others.